Identify the Source of Your Email Leaks and Combat Spam
Written on
Understanding Email Leaks
Have you ever wondered why your inbox is overflowing with spam? Imagine you've registered for various online platforms, and suddenly, unsolicited emails from unfamiliar sources flood in. Your once pristine email account is now a playground for spammers claiming to be wealthy benefactors. Wouldn't you like to uncover the source of these leaks?
I found myself in this very predicament and sought a solution. Not only did I identify the source of the leaks, but I also managed to thwart any future spam attempts. In this guide, I'll walk you through the simple steps I took to resolve the issue, followed by an explanation of the clever email technology that made it possible.
Using Plus Addresses for Sign-Ups
To illustrate, let's say you want to register for a random online service. Instead of using your primary email address, opt for a plus address. Here's how it works:
Imagine your email is: [email protected]. If you're signing up for a music streaming platform, you can provide this address:
No need to worry—emails from this service will still arrive in your main inbox. The part after the plus (+) sign acts as a label rather than a component of your email address.
You can apply this method for other services as well:
- Fictional Service 1: [email protected]
- Fictional Service 2: [email protected]
This approach ensures that each service provider receives a distinct version of your email, while you still access all their communications in one place.
Setting Up Filters and Actions
Depending on your email provider, you may need to create labels manually. Essentially, you instruct your email client to recognize when an email is sent to a specific plus address:
If an email arrives at “[email protected]”, label it as “Fictional Service 1”.
With these labels in place, you can set up automated actions. For instance, instruct your email client to move emails with certain labels to designated folders or delete them outright. This functionality will help you pinpoint the source of spam and take automatic measures against it.
Identifying the Source of Email Leaks
Once your labeling system is operational, any spam emails you receive will carry the label associated with their source. This way, you can quickly identify which service leaked your email.
While you might consider unsubscribing from the offending service, there’s no guarantee that they haven't shared your email with other spammers. Therefore, you can use the filter/action system to manage unwanted emails.
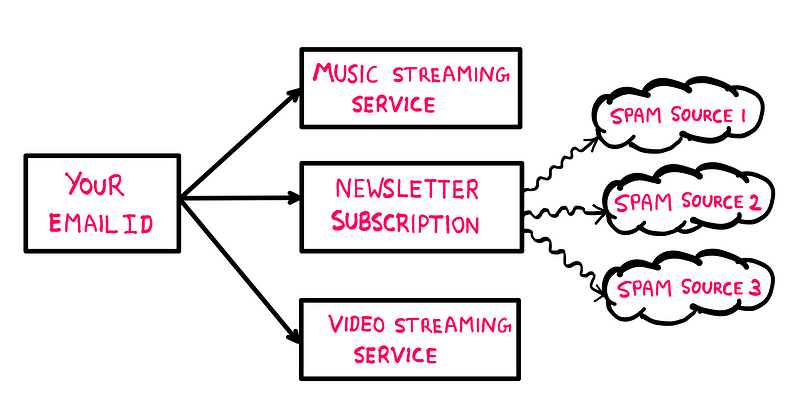
By instructing your email client to automatically send emails from the identified source to your spam folder or delete them, you can effectively neutralize spam attempts without manual intervention.
Understanding Subaddressing
The technique behind this strategy is called ‘subaddressing’ or ‘plus addressing’. In the context of Simple Mail Transfer Protocol (SMTP), email addresses follow this structure:
<local-part>@<domain>
When using subaddressing, the format becomes:
<local-part>+<tag>@<domain>
The ‘+’ symbol allows you to create a unique identifier for each service you register with. Most popular email providers support this feature.
However, there are some limitations to keep in mind when using this technology.
Limitations of Subaddressing
The ‘+<tag>’ you choose must adhere to standard character restrictions of SMTP addresses, such as avoiding spaces. Additionally, some online services may not recognize the plus (+) symbol in their forms. In cases where you need to send an email to unsubscribe, your email's "from" address will default to your main address, which might cause issues with your unsubscribe requests.
How to Effectively Use This Strategy
To summarize the steps discussed:
- Register for online services using a plus address: <local-part>+<tag>@<domain>. Make each tag unique.
- Label incoming emails based on the plus addresses used.
- Identify which spam email corresponds to which label.
- Set up automated filters to manage emails from those sources.
Enhanced Organization for Your Inbox
As an additional use case, you can utilize this method to better organize your email connections. For example, instead of providing separate email addresses to friends and family, you could use:
- For friends: [email protected]
- For family: [email protected]
This concept can extend to business emails as well, allowing you to categorize communications by department, such as ‘Billing’ or ‘CustomerSupport’.
I discovered this effective technology while trying to resolve my own email issues and found it so valuable that I felt compelled to share my insights. I hope you find this guide helpful and enjoy organizing your email sources.
In this video, you’ll learn about five tools that can help you detect data breaches, safeguarding your email and personal information from potential threats.
This video explores how to check if your accounts and passwords have been compromised on various websites, providing essential security measures to protect your data.