Addressing Broken Authentication in Kubernetes Security
Written on
Chapter 1: Understanding Kubernetes Authentication Challenges
In our ongoing exploration of "Kubernetes Security," we turn our attention to the authentication challenges faced within this platform. Authentication, in this context, pertains to verifying the identity of users attempting to access resources, whether they're hosted in the cloud or on-premises. For example, consider an employee accessing organizational resources remotely via SSH. In such a case, the individual must provide valid credentials (username and password) to gain entry to sensitive areas of the organization.
If Kubernetes's authentication system isn't configured correctly, it poses a substantial risk to both the cluster and associated cloud resources. Given the diverse scenarios in which authentication can be applied within Kubernetes, creating an effective authentication framework can be quite complex.
Section 1.1: How Authentication Works in Kubernetes
In Kubernetes, users or services must authenticate before accessing system resources. This process is primarily managed by the Kubernetes API, and the method of authentication—whether it involves an HTTP request or another approach—can vary based on the cluster configuration. Only valid authentication requests are permitted; all others receive a 401 status code. API servers typically validate every incoming request and support two distinct authentication methods.
Subsection 1.1.1: Human Authentication
Users may seek access for various reasons: developers debugging applications, platform engineers testing infrastructure, among others. Since user accounts aren't tied to namespaces, each account operates within its own distinct cluster. Various methods can facilitate authentication, including Cloud IAM policies, certificates, OpenID Connect, or the service account authentication process. The effectiveness of these methods can vary, with some offering more robust security than others.

To ensure that resources are accessed only after appropriate authentication, programs must first authenticate with the API server.
Subsection 1.1.2: Service Account Authentication
Service accounts are mainly used within a cluster to authenticate containers with APIs. These accounts provide the identity for Kubernetes resources. For instance, if a single pod in the cluster possesses an identity, that pod will authenticate other pods to the Kubernetes API server and assign the necessary permissions for Kubernetes API objects.
Chapter 2: The Risks of Broken Authentication
The API is critical in Kubernetes as it mediates communication between applications and their resources. APIs enable not only interactions between applications but also between clusters and end users. They allow developers to query and modify API objects, such as Namespaces, Pods, Events, and ConfigMaps.
For example, a developer might look for a Kubeconfig file in the organization’s GitHub repository. This configuration file contains access credentials for Kubectl, the command-line tool for Kubernetes, indicating that it stores authentication information for any cluster, including necessary certificates. If a hacker gains access to these credentials while scanning the repository, they can potentially exploit them to perform unauthorized actions.
A notable vulnerability, CVE-2020-8559, exemplifies the dangers of broken authentication. An attacker can intercept requests between Kubernetes and Kubelet, manipulating a client into following a redirection request, thereby compromising the client’s original credentials.
Video: Broken Authentication Mechanisms in Kubernetes
Chapter 3: Remediating Broken Authentication
Understanding the importance of safeguarding against broken authentication is crucial, as it can lead to severe exploitation risks. Here are several strategies for remediation:
Implement Multi-Factor Authentication (MFA):
Regardless of the authentication method chosen, it is advisable to adopt a second form of authentication, such as MFA. This way, even if an attacker gains access through one method, they will still require the second set of credentials to access resources, thus enhancing overall security.
Utilize Short-Lived Tokens:
Authentication tokens should have a minimal lifespan. By ensuring that tokens do not remain valid for extended periods, the risk of an attacker successfully using a compromised token is reduced.
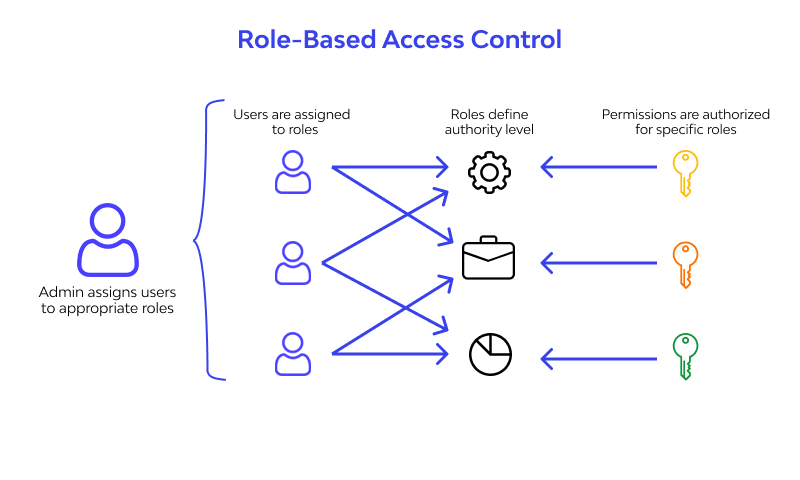
Enable Role-Based Access Control (RBAC):
To address issues of failed authentication, RBAC must be activated within Kubernetes. Although enabled by default since version 1.6, organizations need to implement a more detailed configuration to protect the API. RBAC grants permissions based on user roles, offering a more structured access control mechanism.
Conclusion
The discussion highlights the severity of broken authentication vulnerabilities in Kubernetes, which can grant unauthorized access to the entire cluster. Organizations must prioritize addressing this issue and carefully consider which remediation strategies align with their specific needs and security requirements.
Video: The Hacker's Guide to Kubernetes Security