Ransomware Threats: The Rise of Double Extortion Attacks
Written on
Chapter 1: Understanding Ransomware Attacks
Ransomware has emerged as a significant cybersecurity issue over the past few years, affecting both public and private sectors alike. The topic has dominated headlines, particularly following a series of notable incidents that led to unprecedented ransom demands. A recent report by CipherTrace, a cryptocurrency intelligence firm, sheds light on the evolving landscape of these cyber threats.
In contrast to traditional ransomware, which typically involves the encryption of data until a payment is made, double extortion attacks add another layer of intimidation. Cybercriminals not only encrypt the victim's data but also threaten to release sensitive information publicly.
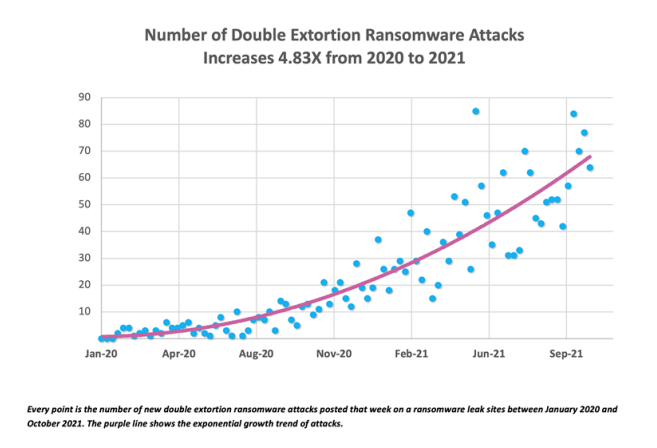
CipherTrace's analysis of cyberattacks from 2020 to October 2021 revealed a staggering increase in double extortion ransomware incidents, with a growth rate of nearly 500%. Here are some key insights from the report:
- The average increase in double extortion attacks was 1.85 times per quarter from 2020 to Q3 2021.
- In 2021, there was a significant uptick in the demand for ransom payments in the privacy-focused cryptocurrency Monero (XMR). Although Bitcoin remained the most requested payment method, it often came with a premium of 10-20% for its use.
- The data indicated that at least 22 ransomware variants exclusively accepted XMR, while 7 accepted both Bitcoin (BTC) and Monero.
- Prominent ransomware groups active in 2021 included REvil (currently offline, possibly temporarily), DarkSide (offline, likely permanently), ContiNews, LockBit 2.0, Pysa, and Dopple Leaks.
- According to FinCEN and corroborated by CipherTrace, ransomware payments in the first half of 2021 were 30% higher than those in all of 2020, totaling approximately $590 million, compared to $416 million the previous year.
Chapter 2: Trends in Ransomware Payments
Security experts from CipherTrace observed a notable shift toward demanding payment in privacy-focused cryptocurrencies like Monero. Hackers have started imposing higher fees for Bitcoin transactions to offset the increased risks associated with using a more traceable currency. The report identified 23 ransomware groups utilizing Monero addresses.
While some groups also request payments in privacy coins such as DASH and Zcash (ZEC), these instances are relatively uncommon. CipherTrace conducted an on-chain forensic analysis of the financial activities of key ransomware players in 2021, revealing various methods employed to obscure their earnings.
Mixers and Coinjoins were frequently utilized—Coinjoins being particularly favored due to their non-custodial nature, despite Mixers providing greater transactional anonymity. Analysts noted that Wasabi coinjoins were the most commonly observed method. Another tactic involved the use of peel chains, where a significant amount of BTC at one address is fragmented through several transactions, each transferring slightly less BTC.
To safeguard against ransomware, a simple backup strategy is no longer sufficient. Organizations must develop a comprehensive incident response plan that includes gathering detailed information about the attackers and the incident, acquiring cybersecurity insurance, using blockchain analytics to trace payments made to cybercriminals, and promptly reporting incidents to law enforcement.
Stay informed with the latest updates—sign up for my weekly newsletter.