Understanding Azure OpenAI Security: Essential Insights
Written on
Chapter 1: The Shift in OpenAI Usage
In recent times, numerous organizations have begun to impose limitations on their employees' use of OpenAI technologies. This trend largely stems from concerns regarding privacy and the security of sensitive data.
Many companies are opting to pause their use of OpenAI until more robust governance measures are established. In contrast, some are transitioning to manage their own self-hosted instances. While self-hosted environments offer greater control and a perception of increased safety for enterprises, they also introduce significant challenges in terms of management. The complexities involved in operating, budgeting, designing, governing, and securing fully self-managed instances can be daunting. Consequently, many organizations prefer services like Azure OpenAI, where the heavy lifting is already taken care of, allowing users to simply set up an instance and pay on a usage basis.
Chapter 2: Trust and Security in Azure OpenAI
Most users of Azure OpenAI typically have an established presence in the Azure ecosystem or Microsoft 365. This existing relationship fosters a level of trust, given that Microsoft manages crucial data such as emails. However, it's essential to scrutinize the finer details of the service agreement.
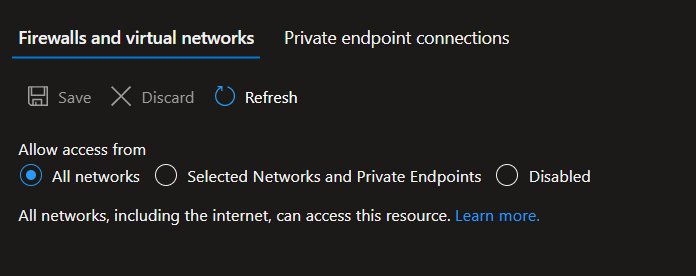
As with many offerings from Microsoft Azure, the default settings tend to prioritize user-friendliness over security. Transitioning from OpenAI ChatGPT to Azure OpenAI means that instances are publicly accessible by default. While this may not pose a significant issue for new deployments, it’s advisable to modify this setting under the networking options to enhance security.
Chapter 3: Key Management and Security Practices
Documentation on authenticating with AzureAD tokens is available; however, many users prefer to work with keys. Upon creating a new instance, you receive two keys similar to those provided for Storage Accounts, which can be utilized for interacting with your deployment. If you choose to rely on keys, it's vital to establish a key management strategy to ensure your security posture remains strong. Even with restricted network access, the risk of breaches persists, as evidenced by frequent news reports of attacks. Regularly rotating your keys can mitigate risks, especially if they are hard-coded in application scripts. Such rotations can also reveal hard-coded secrets, as users often voice concerns when issues arise.
Chapter 4: Logging and Monitoring Best Practices
When operating within Azure, the standard procedure is to navigate to Diagnostic Settings, enable auditing, and direct logs to storage or a log analytics workspace. However, this may not suffice in all situations. Research indicates that typical diagnostic settings may not capture enough data, which again hinges on your organization’s risk appetite. Consider this scenario: it’s a Friday evening, and you suspect a system breach. Your management is demanding answers. Can you clarify:
- What occurred?
- Who was responsible?
- When did it happen?
- From where was the access initiated?
The ability to answer these inquiries is critical, regardless of your position within the organization. If you or your team cannot provide these details, your logging mechanisms may be inadequate.
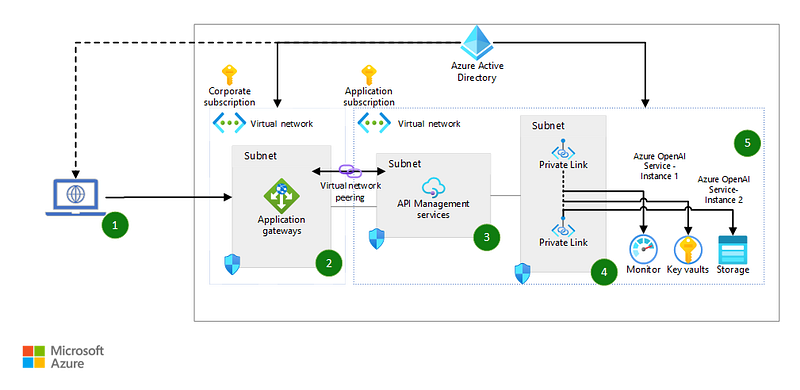
A common approach mirrors Microsoft’s architecture, which channels requests through API Management Services, enhancing logging and security capabilities. Networking tools often collect more detailed information, which can be crucial during incident responses. While not all recommended steps may apply to your situation, it’s wise to simulate basic scenarios to assess your logging efficacy.
The video titled "Azure OpenAI Service - Security, Governance, Use Cases, and Code Walkthroughs" delves into the security measures and governance structures associated with Azure OpenAI, providing practical examples and guidance.
Chapter 5: Conditional Access and Future Insights
Microsoft has categorized the OpenAI Studio as its own application (Azure OpenAI Studio), visible in sign-in logs. This separation allows for enhanced security through the implementation of additional access policies. Keep in mind that network restrictions alone do not determine who can access your system; conditional access policies can further refine access based on user and device profiles.
Although there are ongoing inquiries with Microsoft regarding the classification of OpenAI Studio in their cloud applications, it remains crucial to understand its impact on access control. As the usage of AI technologies expands in enterprises, further insights will emerge to enhance security measures. It’s vital to recognize that we are still in the early stages of this field, and no single entity can claim to be the definitive expert. Different approaches exist, with varying degrees of effectiveness.
While some companies proceed cautiously, Microsoft appears to be aggressively integrating AI across its product suite. My advice is to take the time to understand your use case thoroughly. If working in a controlled environment void of proprietary data, feel free to innovate. However, once confidential information is involved, it's wise to exercise caution. Rectifying technical debts stemming from "innovation tools" can prove challenging, as it may feel like you’re restricting rather than securing your resources. Incorporating security measures from the outset will help minimize friction down the line.

The video "Content Safety for Azure OpenAI - YouTube" discusses the importance of ensuring content safety and compliance within Azure OpenAI applications, highlighting best practices and strategies for implementation.